Shadow IT is not just a disadvantage; it can also be an opportunity to optimize tools across business units.
CapaSystems Blog
Læs
CasesSe et udvalg af vores tidligere projekter og opgaver under Kundecases. Her tilbyder vi dig et indblik i, hvilket arbejde vi kan gøre for dig.
20 Minimum Technical Requirements with a Strict Deadline
Let CapaSystems help you to the finish line with...
IT security is more than just an expensive insurance policy
Outside the IT Department, IT security is...
IT Security Should Be at the VERY Top of Your 2do List
Cyberattacks are NO fun. Thats why it's a good...
Release | Trust is NOT enough!
When it comes to IT security, trusting your users is NOT enough. It is here that Privileged Access Management (PAM) comes into the picture. This is why we introduce AdminOnDemand.
Living on the edge
With AdminOnDemand you can easily assign local administrator rights based on different methods, such as Active Directory group membership or local group membership or assign a user local administrator rights on a single computer.
Say Good-Bye to Outdated and Insecure Rights Management
It does not matter whether you use...

Shadow IT: From Challenges to Opportunities
Shadow IT is not just a disadvantage; it can also be an opportunity to optimize tools across business units.
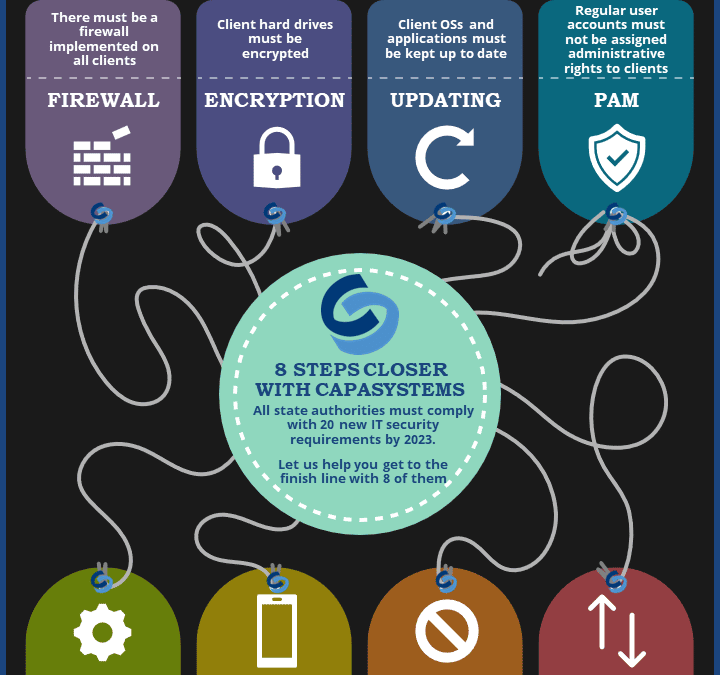
20 Minimum Technical Requirements with a Strict Deadline
Let CapaSystems help you to the finish line with 8 of them...

IT security is more than just an expensive insurance policy
Outside the IT Department, IT security is regarded in an...